Countdown Walkthrough
Scenario
NYC Police received information that a gang of attackers has entered the city and are planning to detonate an explosive device. Law enforcement have begun investigating all leads to determine whether this is true or a hoax.
Persons of interest were taken into custody, and one additional suspect named ‘Zerry’ was detained while officers raided his house. During the search they found one laptop, collected the digital evidence, and sent it to NYC digital forensics division.
Police believe Zerry is directly associated with the gang and are analyzing his device to uncover any information about the potential attack.
Verify the Disk Image. Submit SectorCount and MD5
- The disk image is located at C:\Users\BTLOTest\Desktop\Investigation Files\Disk Image\Zerry
- The below text file is always generated when FTK Imager is used to create the disk image. These details can be used to verify the integrity of the disk image.
What is the decryption key of the online messenger app used by Zerry?
- Launch Autopsy from the desktop and open the Countdown.aut file that's located in the Countdown folder on the desktop.
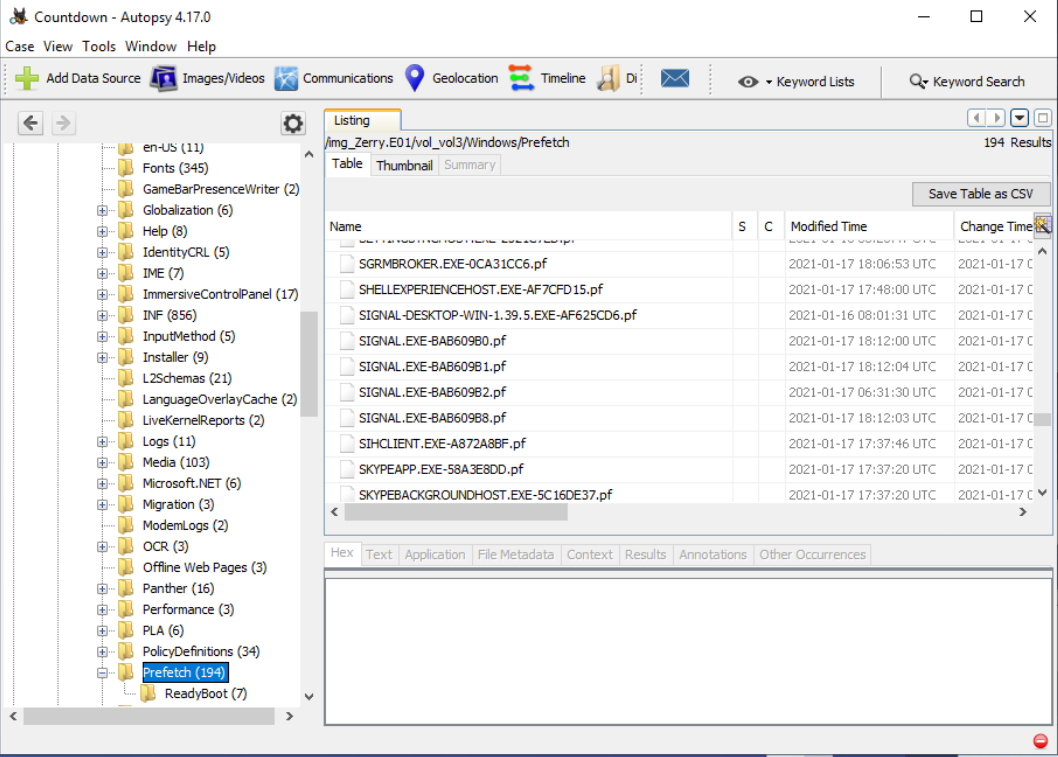
- Before we find the decryption key, we have to figure out the online messenger app that's being used. Once Countdown.aut is open in Autopsy, there's an Installed Programs folder but it doesn't have any instant messaging apps inside of it. From here I went to the Prefetch folder. Prefetch shows what applications have executed. Inside of the Prefetch folder we see SIGNAL.EXE, a known encrypted messaging app.
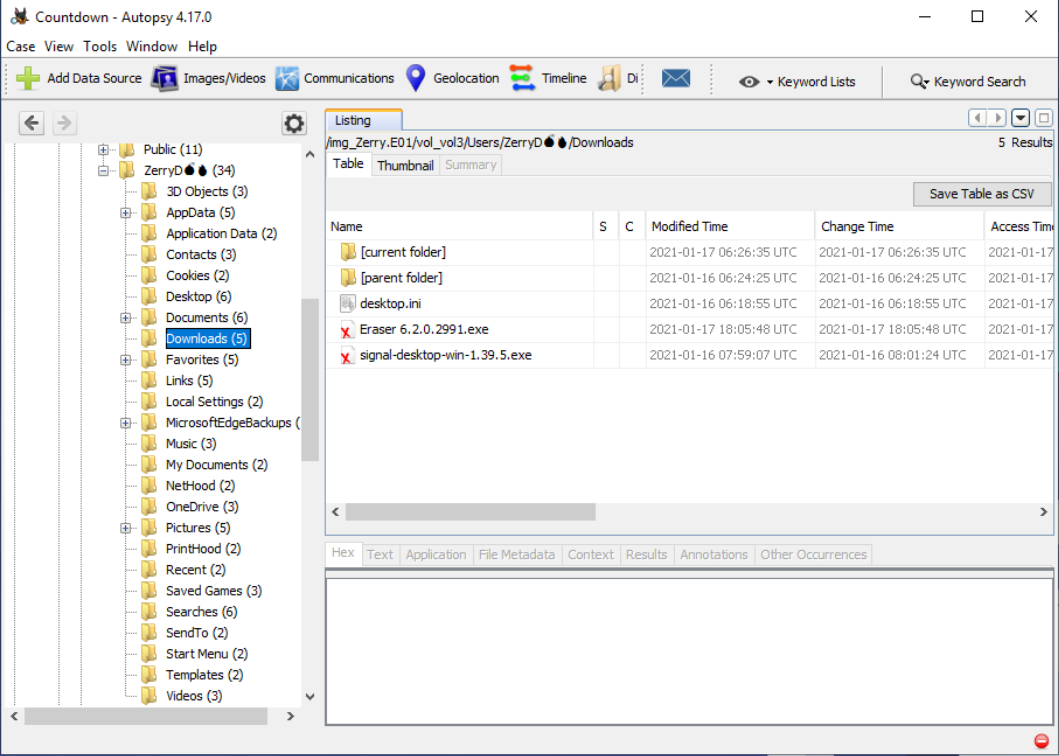
- Just to see if we could find it anywhere else, I also looked in the Downloads folder for the user, Zerry and the Signal exe was there also.
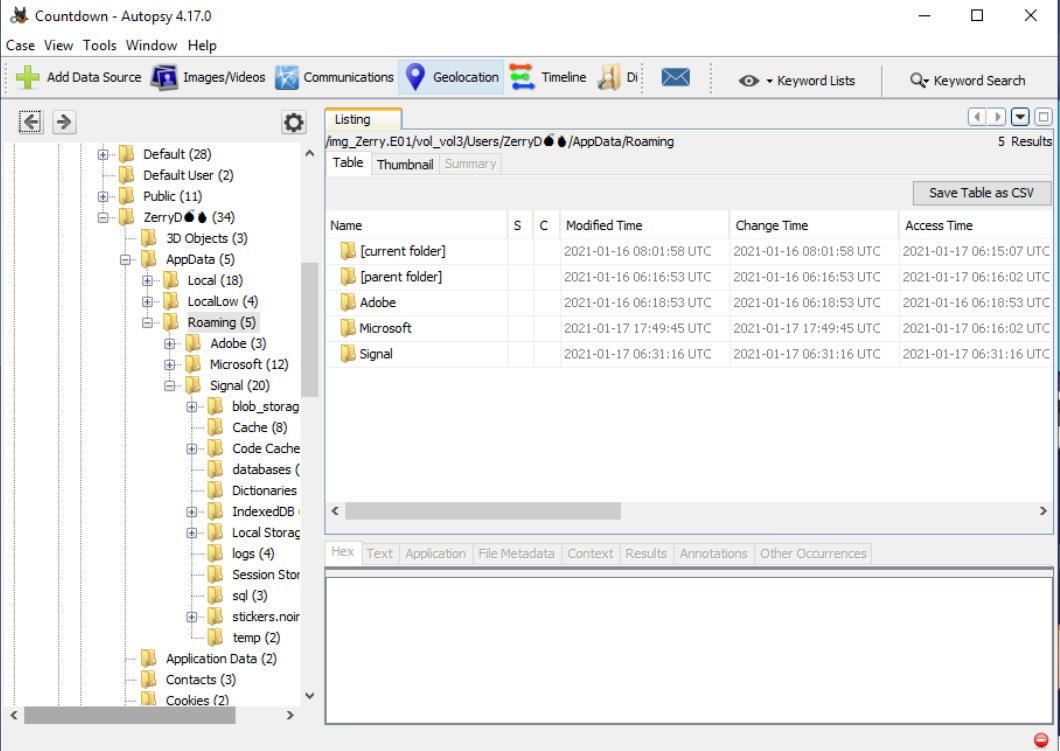
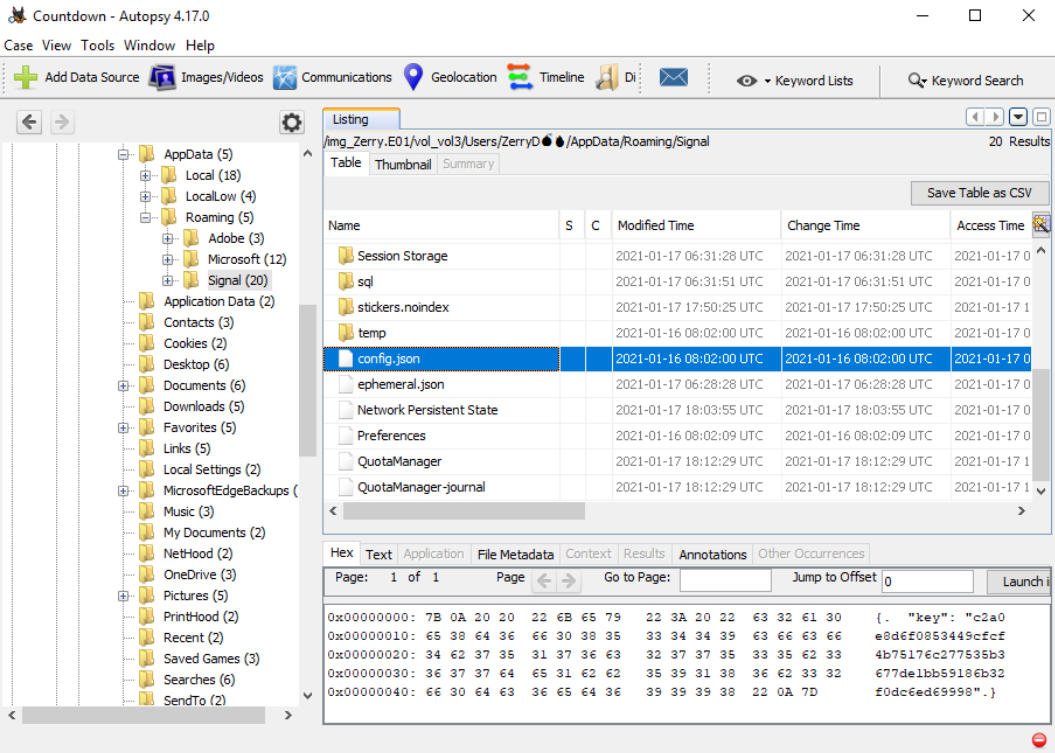
- There's also a Signal folder in the AppData/Roaming folder
- That's 3 places we've found evidence or artifacts of the Signal exe running.
- Now that we've found the encrypted messaging app, we need to find the decryption key. I googled "signal decryption key" and the first result had the answer. The decryption key is located at AppData/Roaming/Signal/config.json. After clicking config.json, the key is in the lower right pane.
What is the registered phone number and profile name of Zerry in the messenger application use?
- We'll use the key we just found to decrypt the file db.sqlite, this is where all of the messages are stored. File is located in AppData/Roaming/Signal/sql. Right click the file and export it to the desktop.
- Now we have to use SQLLiteDatabaseBrowserPortable.exe to open the file db.sqlite and decrypt it. The application can be found in the Investigation Files folder from the desktop. Once you open the application, choose Open Database at the top and choose db.sqlite from the desktop. In the password field, enter 0x before pasting in the decryption key. Also make sure to choose Raw key from the dropdown on the right.
- Now we need the phone number and the profile name. Click the Browse Data tab at the top and then click the dropdown next to Table and choose conversations. Scroll to the right and you'll see the column titled profileName. The phone number is in the e164 column. In order to get the emoji, press Win+ for the emoji keyboard.
What is the email id found in the chat?
- In the dropdown next to table, choose messages. Scroll to the right until you find the body column. Looking in that column for the email address.
Social